CYBERSECURITY AND FOOD DEFENSE
By David E. Bragg, M.S.A.E., Adjunct Instructor, Department of Political Science, Auburn University; Robert A. Norton, Ph.D., Professor of Veterinary Infectious Diseases and Coordinator, National Security and Defense Projects, Office of the Senior Vice President of Research and Economic Development, Auburn University; Marcus H. Sachs, P.E., Senior Vice President and Chief Engineer, Center for Internet Security; Cristopher A. Young, D.V.M., M.P.H., Diplomate A.C.V.P.M., Professor of Practice, College of Veterinary Medicine, Auburn University and Adjunct Professor, College of Veterinary Medicine, Department of Pathology, University of Georgia; and Soren P. Rodning, D.V.M., M.S., Professor and Extension Specialist, Animal Sciences, College of Agriculture, Auburn University
Cognitive Security, a Growing Concern for Food Safety: Part 6
Biosurveillance intelligence, surveillance, and reconnaissance: A detailed description of the system design and operation

Image credit: Igor Barilo/iStock/Getty Images Plus via Getty Images
SCROLL DOWN
The food and agriculture sectors continue to be targeted by adversaries at an alarming rate. These adversaries not only threaten food and water safety, but also the security and continuity of the U.S. food and water supply. While the U.S. food, agriculture, and water industries are incredibly productive and efficient in meeting the increasing demands of a growing global population, they also unfortunately continue to be the most under-protected critical infrastructure in the country.
America's food supply is considered among the most vulnerable and least protected potential targets of attack, according to the Federal Bureau of Investigation (FBI). Farms, ranches, and feedlots are dispersed, open, and generally unprotected.1 Agriculture is the largest user of water worldwide, consuming at least 70 percent of freshwater withdrawals. This high dependence makes the food industry vulnerable to water shortages, droughts, and floods, which can impact production, trade, and food security. Also, agri-food jobs are among the most hazardous, unprotected, and poorly paid. Many agricultural workers lack the rights and legal protections available to workers in other sectors.2
In previous articles of this series, we explored various challenges to food safety including cognitive security,3 business cybersecurity,4 transnational crime,5 threat identification and mitigation,6 and social media.7 In this sixth installment, we look at the design and operation of a proposed Biosurveillance Intelligence, Surveillance, and Reconnaissance (BISR) system to identify and characterize emergent and ongoing threats to the nation's food and water supply chain—from food and water sources to processing and consumption, including transportation and storage—as a vital component of national security. Proper decision-making depends upon vetted (verified as accurate) and timely information. In today's world, information must be supplied at the speed of business.
This article builds upon ideas presented in previous articles describing the integration of artificial intelligence (AI) and sensor-driven data into food safety programs.8,9 While this article describes the architecture of a normally functioning BISR system, it does not address threats from and countermeasures against malformed data, improperly trained AI algorithms, or malicious actors.
ISR Basics
Intelligence, Surveillance, and Reconnaissance (ISR) is defined as follows:
- An integrated operations and intelligence activity that synchronizes and integrates the planning and operation of sensors; assets; and processing, exploitation, and dissemination systems in direct support of current and future operations
- The organizations or assets conducting such activities.10
ISR is traditionally a tool and process used by military and intelligence agencies to address national security problems. The monitoring and protection of the nation's food supply—including potable water resources—is a critical element of national security and, thus, ISR is an appropriate tool and process to apply against threats that are both naturally occurring and malicious. We can apply versions of the technologies that the national security enterprise has developed and utilized against "traditional" threats, especially as many of them are now commercially available and in many ways, superior to legacy classified systems.
A comprehensive BISR system design (Figure 1) stretches from the production of food on farms, ranches, and ponds; through processing plants; and further into warehouses, distributors, and storefronts. Additionally, sensors are included in the various means of road, rail, air, and maritime transportation between each node. Sensors at one or more layers monitor products, processes, and systems as appropriate at each of these nodes, including the transportation links. The most thorough coverage occurs at the origins of the food supply, while a decreasing number of layers are used as food moves through the supply chain to the consumer. In this way, BISR is designed so as not to be intrusive, and consumer privacy is maintained.
FIGURE 1. Biosurveillance Collection and Analysis (Source: Auburn University Research Innovation Center)
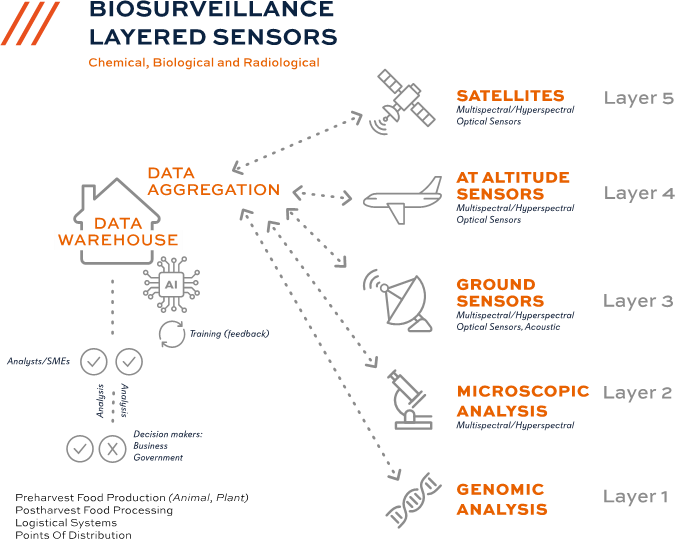
Sensor Types
Common sensor intelligence ("INT") types include:
- Imagery (IMINT). Stand-off observation of farms, ranches, and inside food production facilities, including visible or electro-optical (EO), infrared (IR), ultraviolet (UV), and hyperspectral (HSI) wavelengths; synthetic aperture radar (SAR); light direction and range finding (LIDAR), etc. These sensors can detect a variety of problems, including the presence of pathogens and contaminants, product quality, temperature, and process deviations.
- Tracking and Locating (TAGINT). Radio frequency identification (RFID) and GPS transponders for tags on animals, packages, shipping containers, and vehicles. These are widely utilized already, but can be further developed when combined with differing types of sensors, integrated into serving "pattern of life analysis" of production areas, processing facilities, and supply chain facilities.
- Measurement and Signatures (MASINT). Stand-off and direct environmental sampling at farms, ranches, and inside food production facilities, including air samples, particulate collections, swabs, thermometers, etc.
- Human (HUMINT). Direct sensory observational inputs (photos, text, audio) of an area of interest by a person on the ground, such as a farmer, rancher, fisherperson, veterinarian, butcher, etc. The resulting data is layered into the system outputs of other sensors.
Sensor Layers
Common sensor layers include:
- Layer 5: Space. IMINT and TAGINT. Includes data derived from government and commercially owned/operated satellites already on orbit, such as Landsat 8/9 and the International Space Station. Quick-reaction CubeSats are orbited in response to novel threats (e.g., the presence of influenza virus in avian and/or mammalian species, as alerted by HUMINT or lower-layer sensors), contamination of produce fields, etc. Satellites provide the largest field of view (FOV), but return rates (i.e., latency) of the satellite can range from days to weeks before it passes over the same point on the surface. A higher latency, as with satellites, means slower refresh of data. Conversely, a lower latency, as seen with other layers of BISR, allows for faster refresh of data.
- Layer 4: Airborne. IMINT, TAGINT, and MASINT. Includes data derived from government and commercially owned/operated manned and unmanned aircraft. These platforms have a smaller FOV but a higher resolution. They are deployable to loiter over an area of interest or concern for hours with significantly lower latency. Platforms range in size and payload capacity from man-portable quadcopters to large unmanned and manned platforms such as the RQ-9 Reaper, C-130s, corporate jets, and tethered aerostats.
- Layer 3: Ground/Water. IMINT, TAGINT, and MASINT. Ground and water surface and subsurface vehicles are one example. Their FOV is most restricted with resolutions similar to Layer 4, but can be more stationary during collection. This layer also includes in-person observations, canines, and chemical and biological man-portable sensors such as handheld imagers and air/soil/water samplers. The use of canines and robotic systems can fill in areas unreachable by human observers.
- Layer 2: Microscopic. IMINT and MASINT. Hyperspectral microscopy and chemical and biological laboratory analysis of samples collected in Layers 3 and 4.
- Layer 1: Genomic. Laboratory genomic and molecular analysis of samples collected in Layers 3 and 4 and correlated with analysis at Layer 2. This layer can be a source for libraries of signatures of pathogens and contaminants, including variants used to train artificial intelligence (AI), and for communication between sensors (tipping and cuing) at Layers 3–5.
TABLE 1. Fake Internet Domains Registered as Part of Typosquatting Campaign
“Once AI agents are trained, they can continuously monitor new data against historical data to detect changes and contamination signatures.”


Data Warehousing, Signature Libraries, and AI
BISR requires significant protected data storage to house the long-term current and historical collections of data across the food and water supply network. We recommend the establishment of multiple data warehouses for each food production and processing industry—farming, livestock, poultry, aquaculture, processing, etc.—to focus collections and AI agents on specific issues in each industry with inputs available from the others to consider events such as influenza contamination of poultry or livestock. Once AI agents are trained, they can continuously monitor new data against historical data to detect changes and contamination signatures.
Data Integrity
BISR in Action. "Tipping and cueing" is the ISR process where a "tip" from one sensor layer "cues" another sensor layer to take an alternative look at an area of interest. In simple terms, this is the phrase used to describe the electronic communication between two or more sensors. While ISR is traditionally a top-down process with occasional bottom-up "cueing," BISR is a true bi-directional process.
For example, a rancher at the ground level (Layer 3) sees one or more herd animals behaving erratically in a field. This "tip" might go to a higher or lower layer to see if there is correlation with data collected at that layer. Conversely, overhead sensors (Layer 4 or 5) could show that herd animals are not roaming as expected and cue the rancher to investigate on the ground, perhaps using RFID tag data to examine their movement patterns.
Continuing this scenario, the rancher could submit their observations via an app on their phone, cuing a veterinarian (Layer 3) to obtain a blood sample for microscopic analysis (Layer 2), which is correlated to a known genomic signature (Layer 1) using a trained AI agent. Once a pathogen is identified, BISR cues a collection of HSI (Layer 4 or 5) to determine the extent of infection, whether it be a herd, multiple ranches, or even regions of the country.
Maintaining the integrity of this vast pool of sensor information is extremely important for ensuring food safety, quality, and traceability throughout the entire supply chain. In the food industry, "sensor data integrity" refers to the accuracy, completeness, and consistency of data collected by sensors used to monitor food production, processing, and distribution. It is part of what security professionals refer to as the "CIA triad"—a model of data security that includes Confidentiality, Integrity, and Availability.
Significant amounts of sensor data are collected daily, but this information is not aggregated, organized, and stored in a common system and is not queried in meaningful ways at the speed of commerce. To further complicate matters, the U.S. Department of Agriculture's Animal and Plant Health Information Service (USDA-APHIS) maintains a National List of Reportable Animal Diseases (NLRAD), populated by the unique data systems and unique lists of reportable diseases collected by individual states. Errors in this data can impact food safety and food production systems. The authorities and policies surrounding agricultural commodity data and public health data need to be clarified and codified such that commercially owned technology can be effectively utilized by both the private and public sectors.
As BISR sensors collect data from the multiple layers, they feed the information into the same app the rancher uses, to which the decision-makers can access for near-real-time visualization and analysis of observed and diagnostic data. A good example of a smaller-scale, state-focused biosurveillance is the New Mexico ALIRT system.
“Too often, contamination of processed food is found through food poisoning of consumers. The innovative approach proposed here reduces the likelihood of contaminated food entering the supply chain and reduces the amount of food that must be recalled and destroyed.”


Integrated biosurveillance shortens the decision-making loop to observe, orient, decide, and act (OODA11) on a pathogen earlier in the disease cycle. This allows for faster containment and/or treatment of an outbreak than current reactionary processes, with benefits such as reducing the number of animals that must be quarantined, treated, vaccinated, or euthanized when an outbreak is confirmed.
BISR also functions in food processing at Layers 1–3, where sensors collect data—such as air samples and HSI—continuously inside the facility and are correlated to pathogen signatures in near-real time. Upon detection, processing is immediately halted, contaminated products are subsequently removed, and the facility is sterilized. Too often, contamination of processed food is found through food poisoning of consumers. The innovative approach proposed here reduces the likelihood of contaminated food entering the supply chain and reduces the amount of food that must be recalled and destroyed.
Control and Oversight. The proposed BISR system would allow for continuous monitoring and enhanced protection of the U.S.’ critical food and water supplies using a proactive, adaptive process that would be most effectively managed as a collaborative effort between federal and state agencies, private industry stakeholders, and academia.
Since food and water security is a national security issue, we recommend that oversight of a BISR system of systems reside within the U.S. Department of Homeland Security. Supporting subject matter expertise could be provided by the U.S. Departments of Agriculture and Interior, the U.S. Environmental Protection Agency, and the U.S. Food and Drug Administration, along with their matching state-level agencies, in partnership with food production and processing industry groups and academia.
Food, agriculture, and water systems are increasingly becoming more complex. Whatever the biosurveillance system the U.S. eventually develops, whether BISR or some alternative, agility—meaning the ability to rapidly meet evolving challenges—will be essential in ensuring that the U.S. food supply remains the safest, most readily available, and most economical in the world.
Notes
- The data referred to in this article was obtained using private sector analytical services and databases made available to the authors. The authors sincerely thank those responsible for the analysis.
- Data obtained from private sector sources.
References
- U.S. Federal Bureau of Investigation (FBI). "Protecting Critical Infrastructure." August 20, 2024. https://www.fbi.gov/news/stories/agriculture-threats-symposium-in-nebraska-highlights-safety-measures-to-protect-nations-critical-food-infrastructure.
- Geneva Environment Network. "Food Systems and the Environment." May 30, 2025. https://www.genevaenvironmentnetwork.org/resources/updates/food-systems-and-the-environment/.
- Norton, R.A., C.A. Young, D.M. Gerstein, M. Sachs, A. Whiskeyman, and G.S. Weaver. "Cognitive Security, a Growing Concern for Food Safety: Part 1." Food Safety Magazine October/November 2024. https://www.food-safety.com/articles/9827-cognitive-security-a-growing-concern-for-food-safety-part-1.
- Gerstein, D.M., R.A. Norton, C.A. Young, M. Sachs, and A. Whiskeyman. "Cognitive Security, a Growing Concern for Food Safety: Part 2." Food Safety Magazine December 2024/January 2025. https://www.food-safety.com/articles/9994-cognitive-security-a-growing-concern-for-food-safety-part-2.
- Sachs, M., A. Whiskeyman, R.A. Norton, D.M. Gerstein, and C.A. Young. "Cognitive Security, a Growing Concern for Food Safety: Part 3." Food Safety Magazine February/March 2025. https://www.food-safety.com/articles/10125-cognitive-security-a-growing-concern-for-food-safety-part-3.
- Lancaster, J., T. McCallister, A. Whiskeyman, G.S. Weaver, M. Sachs, D.M. Gerstein, C. A. Young, and R.A. Norton. "Cognitive Security, a Growing Concern for Food Safety: Part 4." Food Safety Magazine April/May 2025. https://www.food-safety.com/articles/10318-cognitive-security-a-growing-concern-for-food-safety-part-4.
- Whiskeyman, A.D., G.S. Weaver, M.H. Sachs, C.A. Young, and R. A Norton "Cognitive Security, a Growing Concern for Food Safety: Part 5." Food Safety Magazine June/July 2025. https://www.food-safety.com/articles/10460-cognitive-security-a-growing-concern-for-food-safety-part-5.
- Norton, R.A., M. Sachs, and C.A. Young. "A Future View of AI-Enhanced Biosurveillance and Comprehensive Food Safety Programs." Food Safety Magazine December 2023/January 2024. https://www.food-safety.com/articles/9110-a-future-view-of-ai-enhanced-biosurveillance-and-comprehensive-food-safety-programs.
- Norton, R.A., M. Sachs, and C.A. Young. "Beneficial AI: Safe, Secure, and Trustworthy Artificial Intelligence for Food Safety." Food Safety Magazine February/March 2024. https://www.food-safety.com/articles/9250-beneficial-ai-safe-secure-and-trustworthy-artificial-intelligence-for-food-safety.
- U.S. Air Force. "Air Force Doctrine Publication 2-0—Intelligence" 2025. https://www.doctrine.af.mil/Doctrine-Publications/AFDP-2-0-Intelligence/.
- OODA Loop. "The OODA Loop Explained: The Real Story About the Ultimate Model for Decision-Making in Competitive Environments." 2025. https://oodaloop.com/the-ooda-loop-explained-the-real-story-about-the-ultimate-model-for-decision-making-in-competitive-environments/.
David E. Bragg, M.S.A.E. is a Research Program Manager and Adjunct Instructor of Intelligence at Auburn University. He is a retired senior intelligence officer and leader with deep expertise in the operational applications and technological quick reaction development of intelligence, surveillance, and reconnaissance platforms and sensors. He received B.S. and M.S. degrees in Aerospace Engineering from West Virginia University, where he specialized in artificial intelligence and unmanned aircraft flight control systems.
Robert Norton, Ph.D. is a Professor and National Security Liaison in the Office of the Vice President of Research and Economic Development at Auburn University. He specializes in national security matters and open-source intelligence, and coordinates research efforts related to food, agriculture, and veterinary defense.
Cris A. Young (COL RET.), D.V.M., M.P.H., Diplomate A.C.V.P.M. is a Professor of Practice at Auburn University's College of Veterinary Medicine and an Adjunct Professor at the College of Veterinary Medicine at the University of Georgia's Department of Pathology. He received his D.V.M. from Auburn University's College of Veterinary Medicine in 1994. He completed his M.P.H. degree at Western Kentucky University in 2005 and is a Diplomate of the American College of Veterinary Preventive Medicine.
Marcus (Marc) H. Sachs, P.E. is the Senior Vice President and Chief Engineer at the Center for Internet Security. He is a retired U.S. Army Officer and was a White House appointee in the George W. Bush administration. His private sector experience includes serving as the Deputy Director of SRI International's Computer Science laboratory, the Vice President for National Security Policy at Verizon Communications, the Senior Vice President and Chief Security Officer of the North American Electric Reliability Corporation (NERC), and the Chief Security Officer of Pattern Computer. He was also the Director of the SANS Internet Storm Center and has co-authored several books on information security. He holds degrees in civil engineering, computer science, and technology commercialization, and is a licensed Professional Engineer.
Soren P. Rodning, D.V.M., M.S., Diplomate A.C.T. is a Professor in the Auburn University Department of Animal Sciences. He specializes in livestock research and provides Extension/Outreach support to farmers, ranchers, veterinarians, State and Federal Department of Agriculture personnel, and other agribusiness professionals focusing primarily on livestock production systems.

